Ok, Sorry for the bad headline. Back to the topic now…
Wintermute was hacked for ~160m a few hours ago. I took a quick look and my best guess is that it was a hot wallet compromise due to the Profanity bug that was publicly disclosed a few days ago by 1inch team.
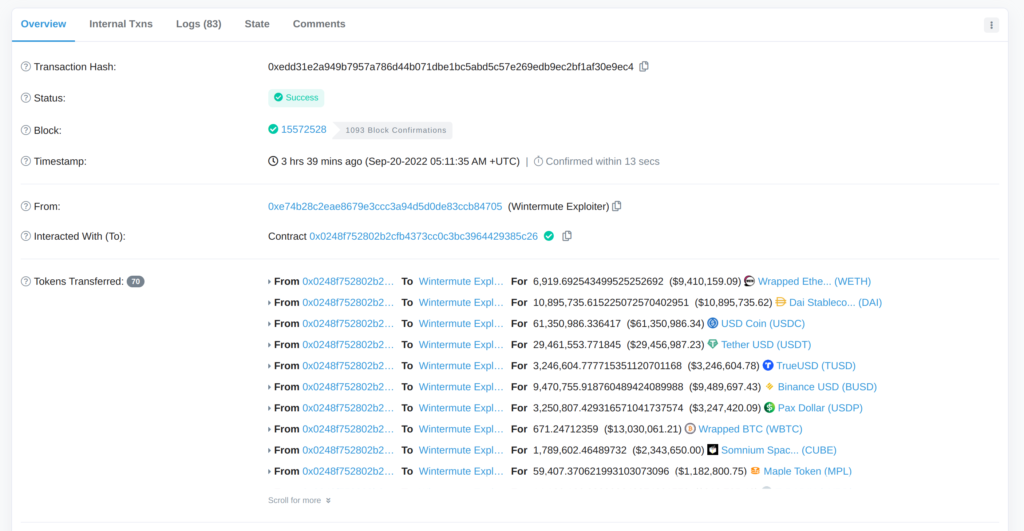
The attack started with https://etherscan.io/tx/0xeecba26d5eb7939257e5b3e646e4bc597b73e256a89cb84a6dfc58de250d8a38 where Wintermute’s hot wallet (https://etherscan.io/address/0x0000000fe6a514a32abdcdfcc076c85243de899b) started calling their vault contract (https://etherscan.io/address/0x00000000ae347930bd1e7b0f35588b92280f9e75) to transfer tokens out to the hacker’s contract (https://etherscan.io/address/0x0248f752802b2cfb4373cc0c3bc3964429385c26)
The vault only allows admins to do these transfers and Wintermute’s hot wallet is an admin, as expected. Therefore, the contracts worked as expected but the admin address itself was likely compromised.
The admin address is a vanity address (starts with a bunch of zeroes) which might have been generated using the famous but buggy vanity address generating tool called Profanity. Profanity has a critical bug that was disclosed by 1inch a few days ago.
Around the time that the disclosure happened, wintermute removed all ether from this admin address (https://etherscan.io/tx/0x93716f3e3a9e3f47dec05b4df511e07e53b3e4695e84cd4f05f5d83188f3552a) which suggests that they realized it might have been vulnerable. However, they forgot to remove this address as an admin from their vault.
The attacker funded this address using their own ether (https://etherscan.io/tx/0x93eadb28e6b50e7ed14348a14cfc3c9f09618dace9c20d3f39ab3d5828e3fd21) and then used this address to pull off the heist. All of it suggests that the attacker exploited the bug in Profanity to recover the private key of this hot wallet.
The attacker is likely a seasoned hacker/solidity developer. They created a helper contract, deposited stables into curve to avoid blacklisting, and figured out this vulnerability in a closed sourced vault contract in the first place. ps. I was again asleep when this happened.
Wintermute said they are still solvent and healthy so there’s no need to panic.
This was originally meant to be just a twitter thread with early analysis but twitter is hiding all tweets with links to etherscan so I was forced to write this blog…..